Query Permissions
Overview
The database implements row-level security to ensure that users can view only records that belong to an entity that they are authorized to access based on entity permissions.
The row-level security is enforced in all types of queries by filtering rows at the time they are read from the database.
As a result, the same query executed by different users can produce different result sets.
Scheduled SQL queries are executed with All Entities: Read permission and are not filtered.
Example
The following example demonstrates how query results for different users are filtered based on the user's effective entity permissions.
Configuration
| Username | Member Of | Allow Entity Group | Entities |
|---|---|---|---|
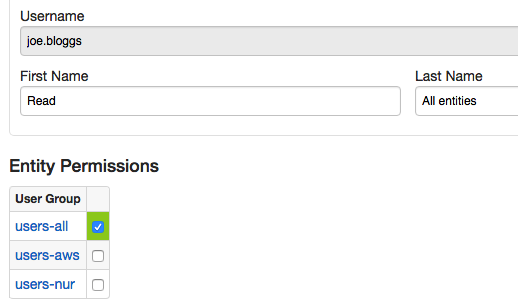
joe.bloggs | users-all | * (all) | * (all) |
jane.doe | users-aws | srv-aws | nurswg* (5 entities) |
john.doe | users-nur | srv-nur | awsswg* (3 entities) |
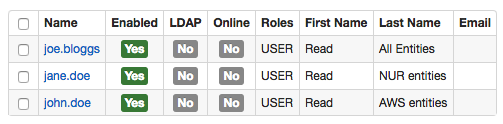
The joe.bloggs user is a member of the user group that has All Entities: Read permissions.
The jane.doe user is a member of the users-nur user group that is allowed to read data for srv-nur entity group.
The john.doe user is a member of the users-aws user group that is allowed to read data for srv-aws entity group.
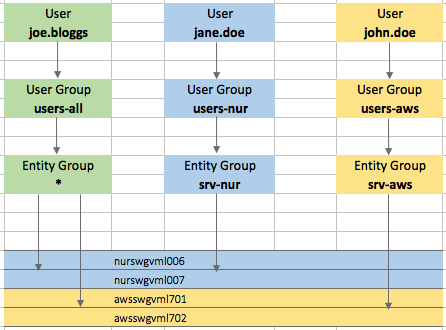
Users
- All users:
- User
joe.bloggs:
- User
jane.doe:
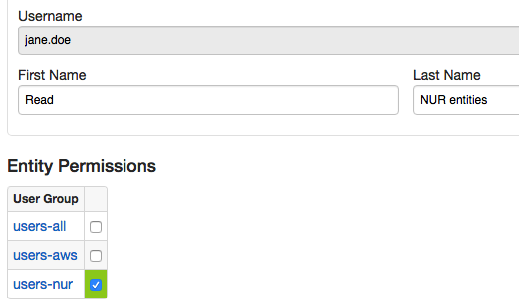
- User
john.doe:
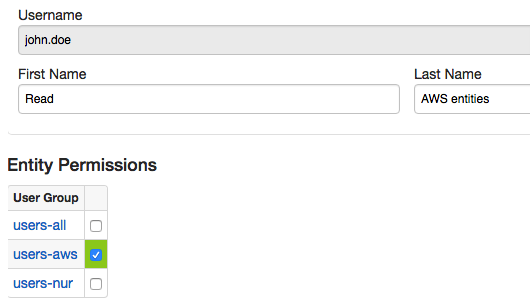
User Groups
- User Group
users-all:
- User Group
users-nur:
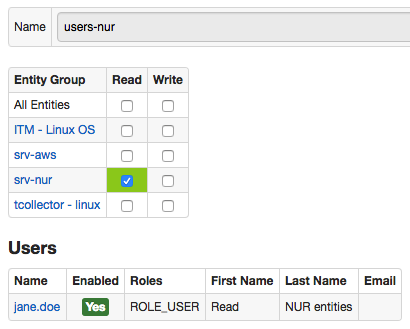
- User Group
users-aws:
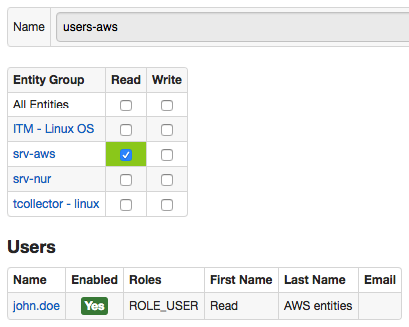
Entity Groups
- Entity Group
srv-nur:
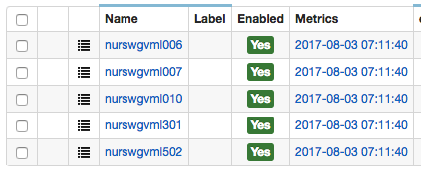
- Entity Group
srv-aws:
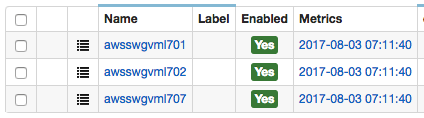
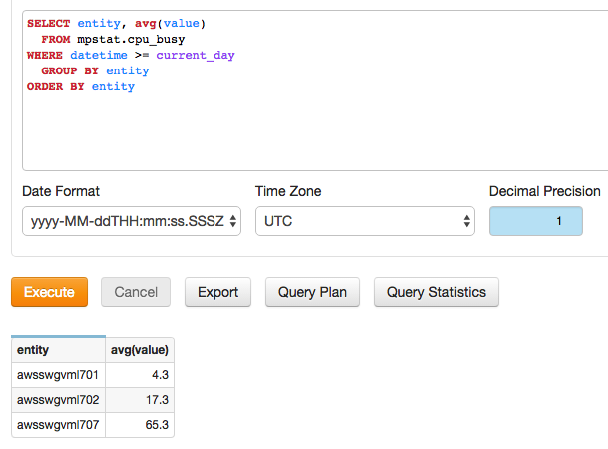
SQL Query
SELECT entity, avg(value)
FROM "mpstat.cpu_busy"
WHERE datetime >= current_day
GROUP BY entity
ORDER BY entity
Query Results
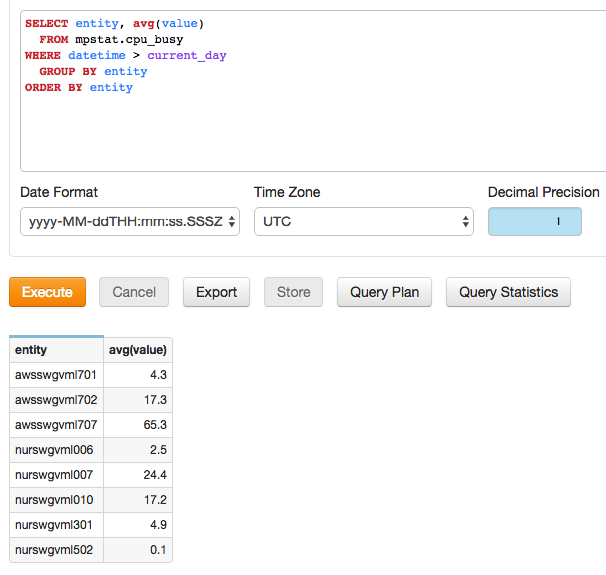
- Results for user
joe.bloggs:
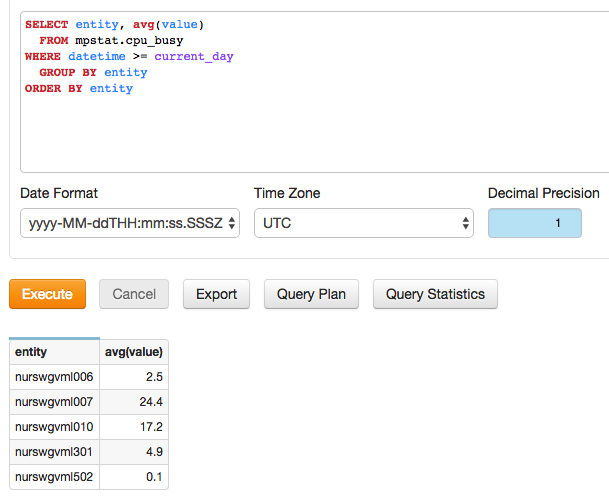
- Results for user
jane.doe:
- Results for user
john.doe: