AWS IAM Account for CloudWatch
Overview
This document describes the process of creating a read-only account used to query statistics from AWS CloudWatch API.
Account Configuration
Create User Group
Log in to the AWS Console and locate the IAM (Identity and Access Management) service under the Security, Identity and Compliance section.
Open the Groups menu and click Create New Group.
Specify group name, for example cloudwatch-ro-group.
Create User
Open the Users page and click Create New User.
Enter a user name such as cloudwatch-ro-user.
Generate access and secret keys for the user. Copy the keys for your reference.
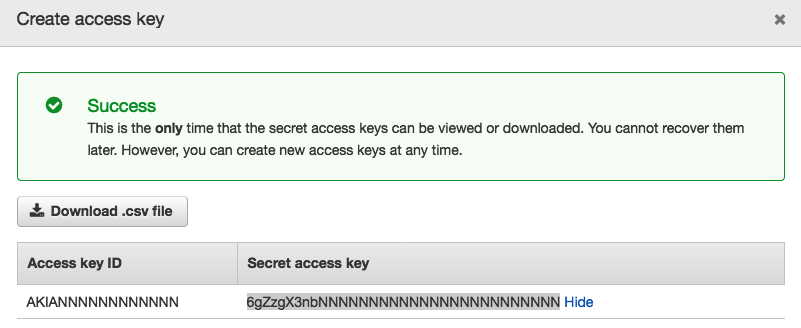
The keys are required for the AWS Job in Axibase Collector.
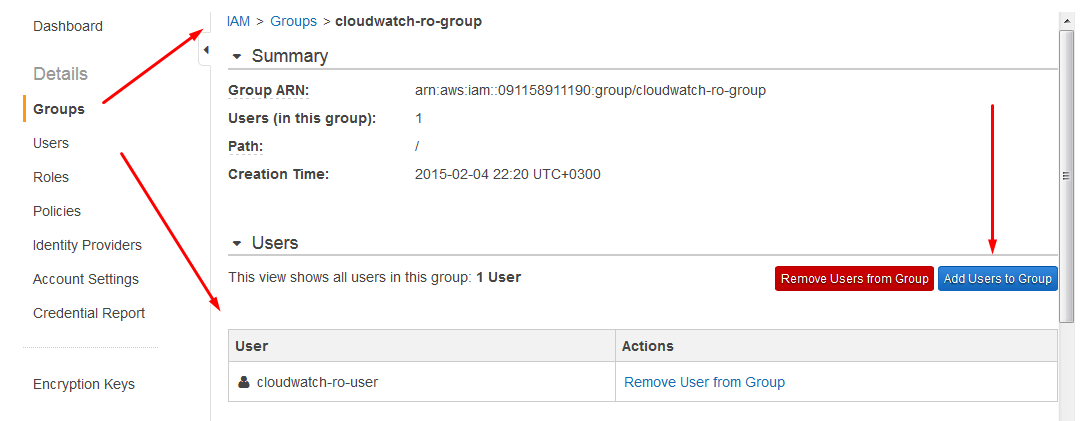
Add User To Group
Open the Group page and click Add Users to Group.
Add cloudwatch-ro-user to the cloudwatch-ro-group.
Grant Permissions
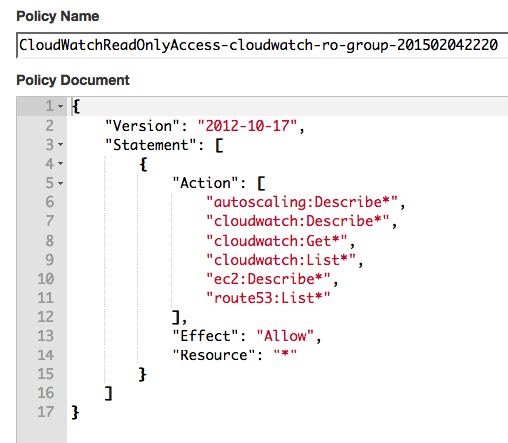
Open the Group page and click Create Group Policy
Enter the following policy text in JSON format, click Validate Policy and save the configuration.
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"cloudwatch:List*",
"cloudwatch:Get*",
"cloudwatch:Describe*",
"ec2:Describe*",
"autoscaling:Describe*",
"route53:List*"
],
"Effect": "Allow",
"Resource": "*"
}
]
}
The above policy grants users in the cloudwatch-ro-group permissions to execute various GET, LIST, and DESCRIBE API methods. This type of policy grants read-only access.
The cloudwatch: actions are required to list available CloudWatch metrics and download statistics, whereas actions for the other namespaces are required to download AWS resource attributes and relationships and store them as metadata in ATSD.
To simplify configuration, use wildcards to grant multiple actions using prefix matching. For example, specify route53:List* action instead of route53:ListHealthChecks and route53:ListTagsForResources.
Sample namespace-specific actions:
ec2:DescribeInstancesec2:DescribeVolumesautoscaling:DescribeScalingPlansautoscaling:DescribeScalingPlanResourcesroute53:ListTagsForResourcesroute53:ListHealthChecks
You can now query Amazon CloudWatch APIs with the new user account, access key, and secret key.